Accuray Product Cybersecurity
Accuray is Dedicated to Cybersecurity
Cybersecurity is a comprehensive and ongoing lifecycle process that is of the utmost importance and priority for Accuray.
Accuray is dedicated to ensuring the safety and security of our products so that you can confidently deliver the best possible care to patients. Our products employ a multi-modal approach to security that includes People, Process and Technology to address the ever-increasing risk of cyber threats. To that end, we have created a Security Advisory archive to keep you informed of cyber-security risks and the actions being taken by Accuray.
Our commitment to this full cybersecurity lifecycle process ensures that our customers can trust us, and that we remain resilient against evolving threats.
Accuray also encourages customers and other interested parties to report Accuray security concerns to their respective Technical Support Representative, or via: https://www.accuray.com/contact-us.
To view all vulnerability disclosures please click here. If you are not an Accuray Exchange member and are an Accuray System user, join now.
Cybersecurity Policy Statement
Accuray recognizes that trust is essential for organizations and customers to fully embrace and benefit from our technologies. We are committed to providing customers with secure radiation treatment products they expect, and to have confidence in Accuray as their preferred radiation therapy product provider. Our cybersecurity policies and practices are continuously evolving to harmonize with leading industry standards, complementing more than two decades of experience in delivering innovative, life saving, and reliable products.
Cybersecurity is a critical element in Accuray’s approach to securing its computing environment. In an ever-changing threat environment, our development teams strive to employ rigorous cybersecurity practices, which are imbedded into Accuray’s Secure Development Lifecycle (SDL). The SDL process is now integrated with the product development lifecycle from requirements to design to implementation. Various phases of the SDL process emphasize secure software development practices, and dictate specific activities and processes be applied as appropriate to each phase of product development.
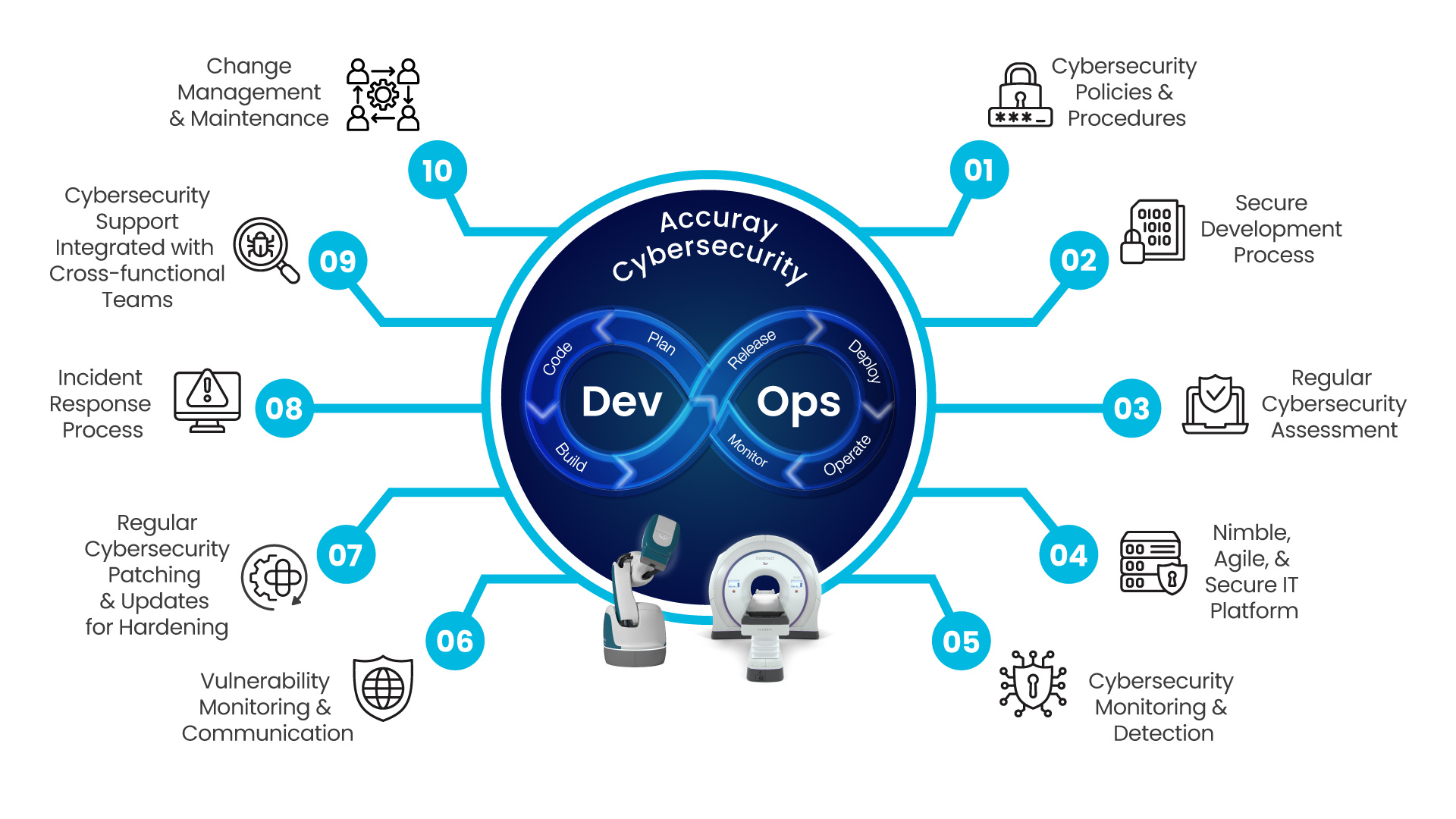
From inception and implementation, to maintenance, we prioritize security at every stage of our process. Our approach begins with administrative controls such as policies and procedures, followed by robust design and assessment, and continuous monitoring to identify vulnerabilities. We apply security patches and updates, conduct routine penetration testing, and offer regular training to foster a security-conscious culture. Our incident response plan is designed to address any security breaches or incidents and integrate with cross-functional teams for timely support. Our process continues to be updated and improved through the change control process.
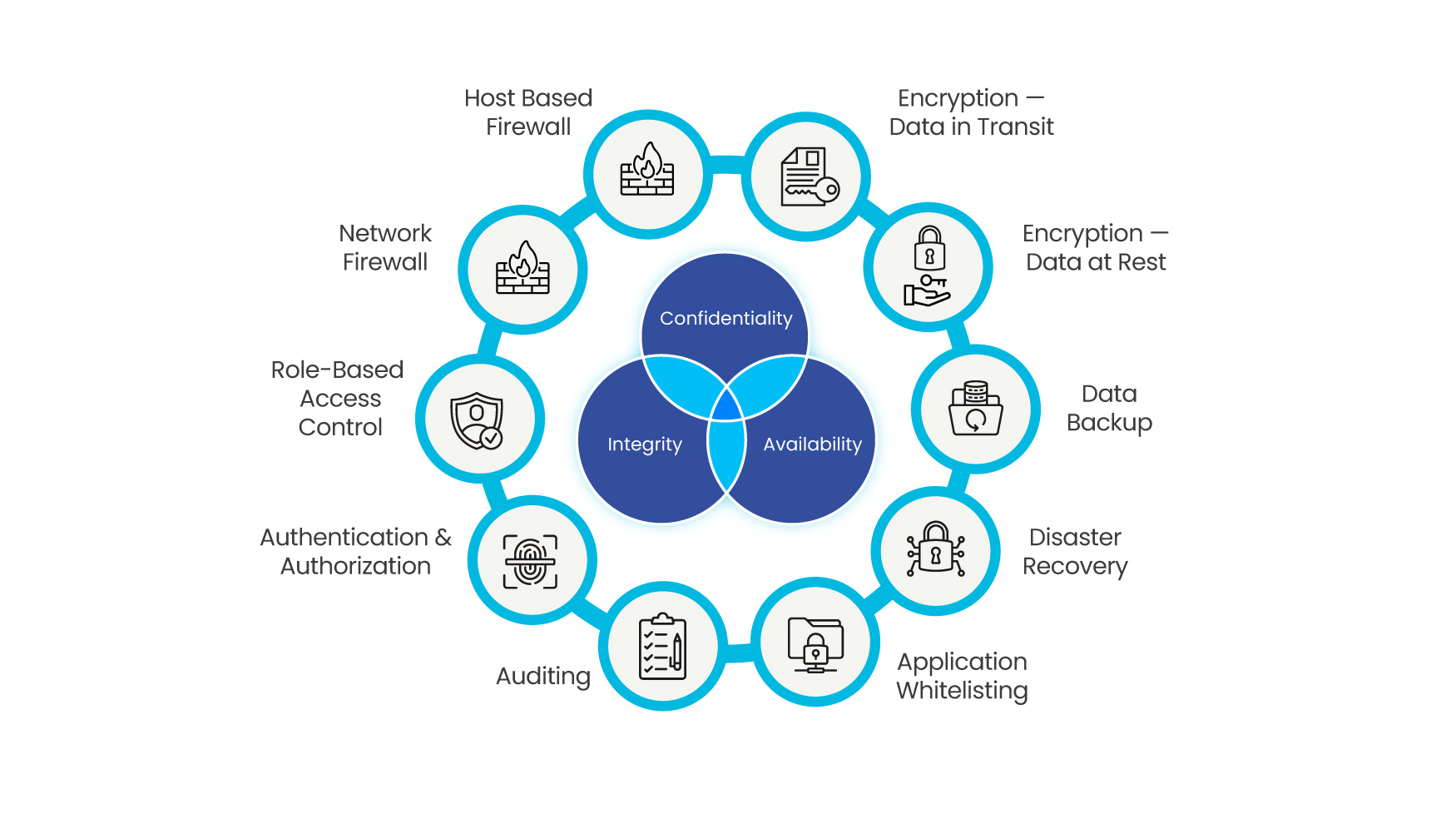
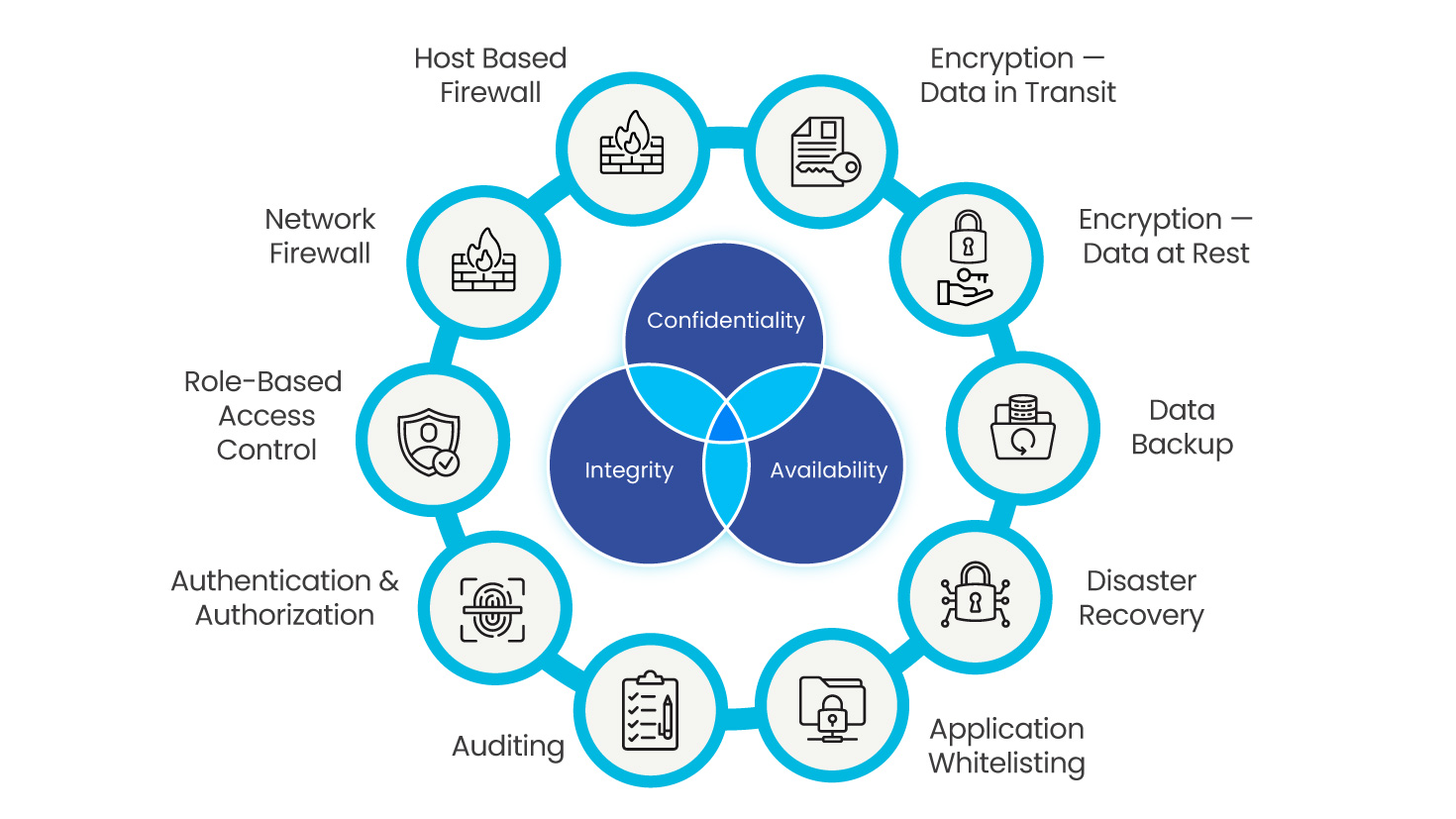
Software-based firewall deployed in Windows device sets security rules on device’s inbound and outbound communications.
The Accuray Firewall by default blocks all inbound and outbound communications. Only approved communications via Access Control Lists (ACLs) are allowed to traverse from Accuray to Hospital network and vice versa. Accuray-provided and managed firewall device provides a single exit and entrance point between the hospital network and the Accuray private LAN.
The iDMS employs a built-in role-based authentication system to grant or deny access to certain features and functions based on user role.
Each user is assigned a login account and password. Each login account is associated with a role or profile that defines what the user can do. Customer administrator can manage accounts, make changes to the user profiles and set policies to meet their security requirements.
User activities are audit-trailed at application, OS and firewall levels.
Application whitelisting tool is deployed on all Windows-based machines to protect against and prevent unknown executables, scripts, and batch files from running.
Data is backed up every 2 hours and disaster recovery option is provided for critical devices.
Data is backed up every 2 hours and disaster recovery option is provided for critical devices.
Data at Rest – Microsoft BitLocker technology using Advanced Encryption Standard (AES) with a key length of 256 bits to protect the contents of hard drives that contain PHI data at rest.
Data in Transit – Data communication with PHI data is encrypted using TLS 1.2 encryption.
Software-based firewall deployed in Windows device sets security rules on device’s inbound and outbound communications.
The Accuray Firewall by default blocks all inbound and outbound communications. Only approved communications via Access Control Lists (ACLs) are allowed to traverse from Accuray to Hospital network and vice versa. Accuray-provided and managed firewall device provides a single exit and entrance point between the hospital network and the Accuray private LAN
The iDMS employs a built-in role-based authentication system to grant or deny access to certain features and functions based on user role.
Each user is assigned a login account and password. Each login account is associated with a role or profile that defines what the user can do. Customer administrator can manage accounts, make changes to the user profiles and set policies to meet their security requirements.
User activities are audit-trailed at application, OS and firewall levels.
Application whitelisting tool is deployed on all Windows-based machines to protect against and prevent unknown executables, scripts, and batch files from running.
Data is backed up every 2 hours and disaster recovery option is provided for critical devices.
Data is backed up every 2 hours and disaster recovery option is provided for critical devices.
Data at Rest – Microsoft BitLocker technology using Advanced Encryption Standard (AES) with a key length of 256 bits to protect the contents of hard drives that contain PHI data at rest.
Data in Transit – Data communication with PHI data is encrypted using TLS 1.2 encryption.

Software-based firewall deployed in Windows device sets security rules on device’s inbound and outbound communications.
The Accuray Firewall by default blocks all inbound and outbound communications. Only approved communications via Access Control Lists (ACLs) are allowed to traverse from Accuray to Hospital network and vice versa. Accuray-provided and managed firewall device provides a single exit and entrance point between the hospital network and the Accuray private LAN
The iDMS employs a built-in role-based authentication system to grant or deny access to certain features and functions based on user role.
Each user is assigned a login account and password. Each login account is associated with a role or profile that defines what the user can do. Customer administrator can manage accounts, make changes to the user profiles and set policies to meet their security requirements.
User activities are audit-trailed at application, OS and firewall levels.
Application whitelisting tool is deployed on all Windows-based machines to protect against and prevent unknown executables, scripts, and batch files from running.
Data is backed up every 2 hours and disaster recovery option is provided for critical devices.
Data is backed up every 2 hours and disaster recovery option is provided for critical devices.
Data at Rest – Microsoft BitLocker technology using Advanced Encryption Standard (AES) with a key length of 256 bits to protect the contents of hard drives that contain PHI data at rest.
Data in Transit – Data communication with PHI data is encrypted using TLS 1.2 encryption.
Have questions or concerns?
To ask questions or raise a concern about company activities and business, contact Accuray here.